ISO 27001 checklist for HR and IT systems
As a controller of your Personally identifiable information (PII) of your employees and customers, companies have the responsibility protect that data with due care, subject to requirements such as GDPR and the ICO.

But keeping data safe is easier said than done. 88% of UK companies have suffered breaches in the last 12 months and with an average damage of £16k per breach for SMEs in the UK, they don’t come cheap.ISO 27001 is a good way to signal to customers and investors that you are taking this seriously and to make sure you are acting responsibly to keep their data safe. And to protect yourself from potential damages and fines as a result of not acting with due care.
Is my company at risk of data breach ?
Most likely, yes. You may not be aware but most companies are at risk and data breaches can have serious consequences causing financial harm to you company, your employees and your customers.According to Varonis, most companies are targeted by phishing attacks and are at risk for example due to improper use of email used as a medium to exchange PII. Let’s admit it, we are all doing it, some of us to a lesser and some of us higher extent.
- 95% of cybersecurity breaches are caused by human error
- 90% of data breaches are caused via email
- 88% of organisations worldwide experienced spear phishing attempts in 2019
- 37% (top) malicious email attachment types are .doc and .dot which appear harmless
We all know we should do better as it makes us vulnerable and a small mistake as simple as losing an unprotected laptop could expose all sensitive information a company possesses to people that will do everything for a financial gain.
What are the consequences of a data breach UK?
Research from Sophos shows that phishing and ransomware attacks have doubled in the last 2 years only. In the last year 66% of companies were attacked by ransomware compared to up 37% in 2020.Most companies do not have insurance that covers the damages and with an average damage of £16k for a UK SME per breach, the cost is meaningful.Additionally, if you are found to not have acted with due care, the UK’s regulatory body for data protection ICO can issue a fine of up to the higher of £17.5 million and 4% of your total annual revenue.
What can I do to keep PII data safe and protect myself from data breaches?
If you want to be ready for an ISO 27001 audit (or SOC2 audit) or if you simply want to improve the way that you handle and protect sensitive information in your company, using modern software that embeds security right into your existing employee operations processes is a great way to do so.
That is because ISO 27001 requires certain controls for HR and IT processes to be in place, and using the right software avoids adding overhead to the business. This includes HR software, payroll and software used to manage your IT, such as device management and access control.
An increase in digitising and automating employee operations also significantly reduces the risk factor of human error, which is the cause of most data breaches.
The following section give an overview of how you can handle PII with due care and reduce the risk of data breaches resulting from incidents including.
Accidental data breach
For examples caused by exporting data and sharing it with someone you should not have unintentionally (e.g typo in email recipient).
Malicious internal data breach
For examples someone you fired downloaded leads or code and took them to a competitor or sold them online.
Phishing
Phishers have become very professional and can easily impersonate an employee, your accountant or even your CEO to get someone in your company to share or change sensitive information, such as
- change someone’s bank account information to reroute salary to own account
- send tampered wire instructions to your finance team, incl. wires to their own account
- get a list of employee data to sell it to scammers (used for identify fraud, wire fraud, etc.)
Handling of employee data (PII)
Why it is how you handle PII important
- You are the controller of your employees’ PII which gives you responsibilities (GDPR, ICO, ISO, etc.)
- PII includes data like address, bank account information, compensation, national insurance numbers, passport copies, date of birth, emergency contact details and more – it is one of or even the highest risk data you control in your company
- PII can cause harm to employees if it gets in the wrong hands. Especially in the case of phishing it is highly likely the phisher will attack your employees with scams like identity fraud or wire fraud
- Data beaches that can cause harm need to be reported to the ICO and you may be fined if it concludes you did not act with due care
What you need to do
- Never share PII via email and particularly not with external parties such as accountants unprotected. This carries high risk of accidental data breach (small typo in recipient + google autocomplete happens often) and phishing. 90% of all data breaches are via email
- To handle data with due care you need to either let employees input data themselves where you need it, or make sure the data is password protected or encrypted before sharing via email or use an access-restricted cloud drive
How Zelt solves it
Zelt is the single interface for all employee data, and we take data protection extremely seriously. Personal data is provided and kept up to date by employees themselves and it never leaves the platform. Any external parties such as accountants can be given access and you can determine precisely what they can see or not see, and you can easily take away access again. This removes the use of emails for PII exchange and significantly reduces risk.
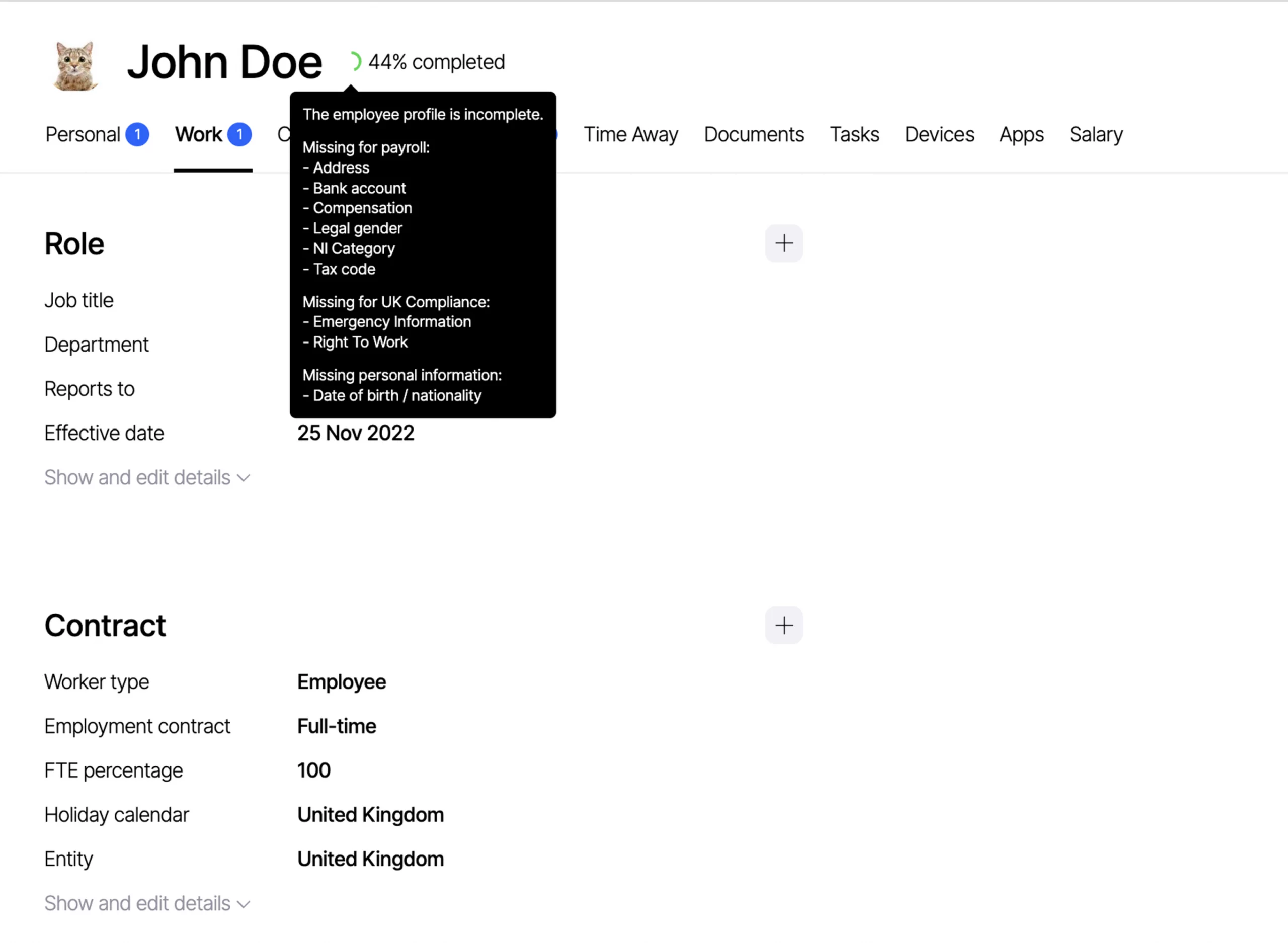
Employee access to company systems
Why it is important
- Company systems contain sensitive and valuable data, that many different types of people would like to get access to for different reasons, usually financial ones
- If a data breach occurs because you did not act with due care you can be made liable for the damages caused by them (I received £3,000 from BA for their last data breach).
- The more people have access rights they should not have, the higher is the risk of a breach, especially for users not aware of the risks. Risks include
What you need to do
- Have a system in place that allows you to oversee what access an individual has to all company systems at a given time and at what permission level (Google, Github, AWS, Hubspot, Intercom, Quickbooks, Slack, etc.)
- Ensure and monitor continuously that people have access on a needs basis (zero trust) and in particular that no-one has access that they should not have (e.g. former employees or someone who needed access briefly but not anymore)
- Keep an eye on high risk access, e.g. a consultants to your AWS or accountants to your employee data, and adjust access to the minimum needed at a given time
- Be able to shut off access to all company systems for a person quickly when needed (e.g. if you fire someone or they lost their laptop)
How Zelt solves it
Zelt lets you connect software used within your company, such as Google Workspace, Github, Hubspot or Slack, so that you can see who has access to what and to what extent, make changes with the click of a button. Not only can employees request access via Zelt themselves, but Zelt keeps a log of who granted access and automatically reminds you to remove all access when you off-board an employee.
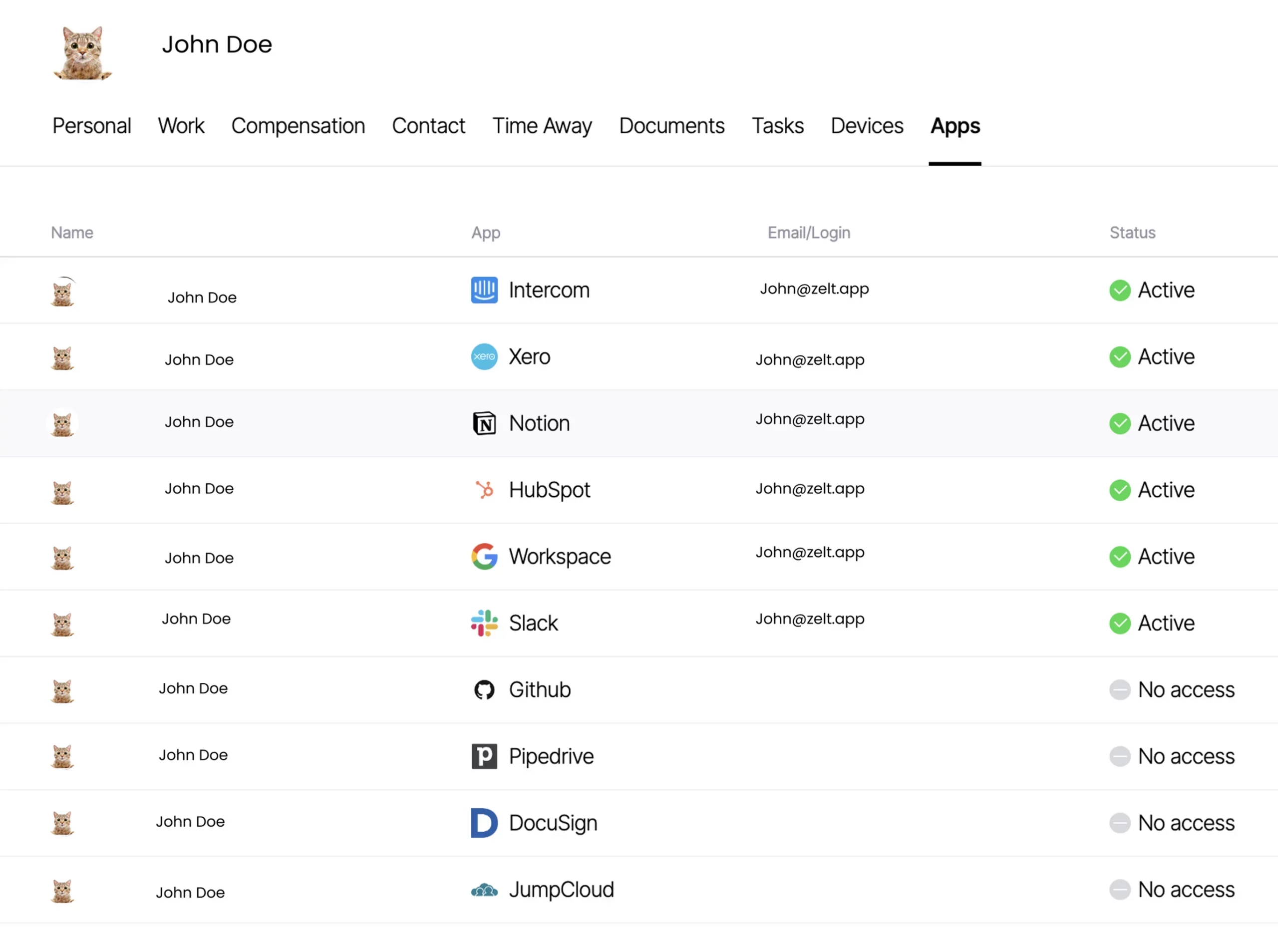
Security of employee company devices
Why it is important
- Laptops that do not have a password can be used to gain access to sensitive company systems by unauthorised users (e.g. if stolen) and result in a data breach and cause harm to the company e.g. if person deletes your Hubspot account or your AWS environment, or sells your leads and customer lists to a competitor
- Every lost or stolen device that is not password protected and encrypted is likely to be a data breach because data on the device may include sensitive information including PII stored on it locally
What you need to do
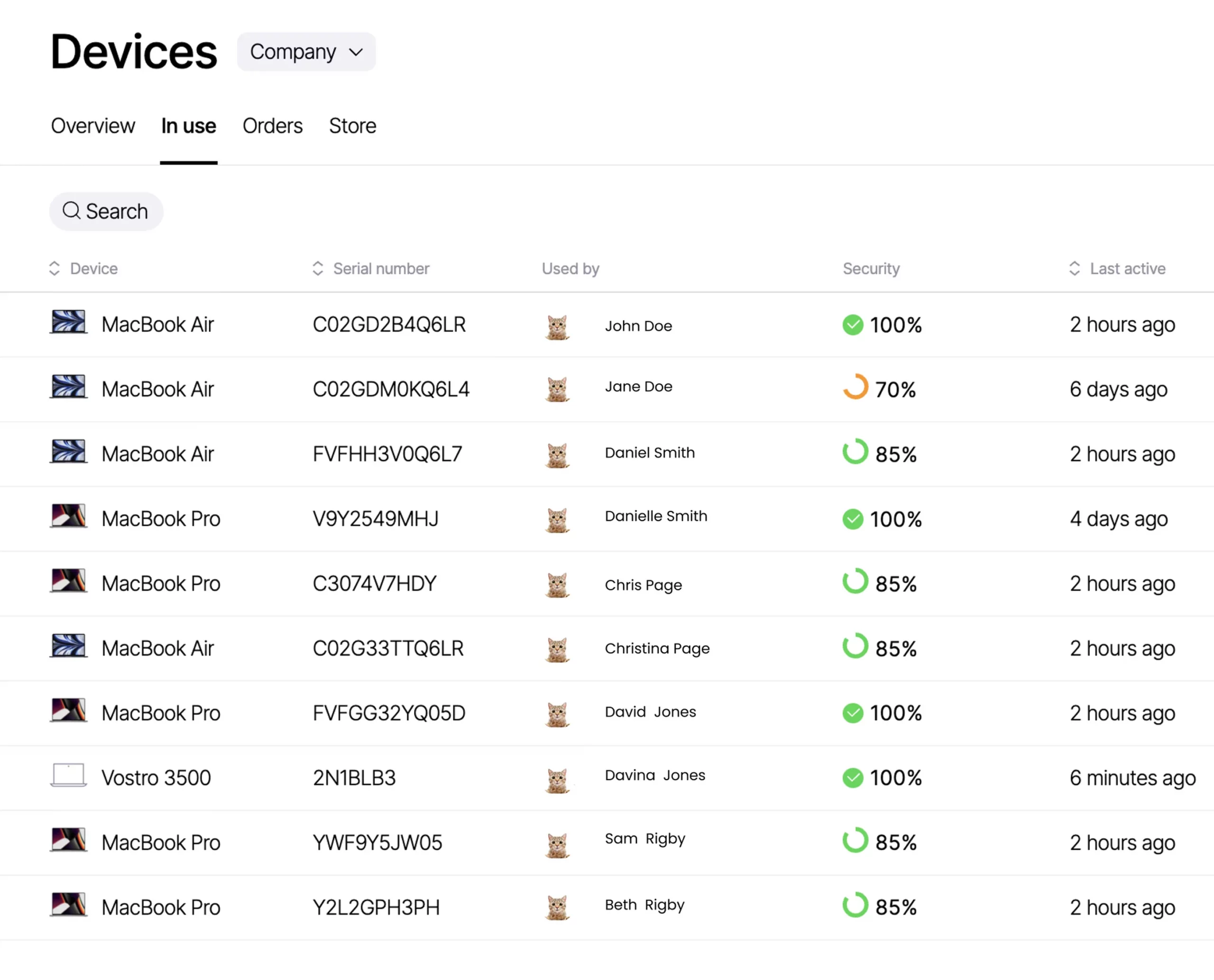
- Maintain real-time asset register with all company devices, its details, who has access to it and how they are secured
- Endpoint secure all company devices, including forcing password rules, device encryption, installation of anti-virus software, monitoring status of updates and forcing updates
- Be able to remotely lock or wipe a device at risk, e.g. if lost or stolen or if employee is fired
- Use zero touch deployment to ensure that every device is adhering to your company policies from the moment of activation
How Zelt solves it
Zelt lets you connect your company and BYOB devices used by employees to the platform which allows you to maintain a real-time asset register and see who has access to which device. Zelt’s MDM functionality lets you enforce security settings including password protection, encryption and OS updates, and perform remote actions such as wiping or locking a device when you off-board an employee or a device gets lost.
Use Zelt to handle data with due care
If you are preparing for an ISO 27001 audit or SOC2 audit or just like to improve the way you handle and protect sensitive information in your company, the best way to do it is using modern software that embeds security right into your existing employee operations processes.Zelt is a next-generation employee platform that enables you to do just that without changing the way you work or adding any friction to your team. If you’re considering starting your ISO 27001 implementation, take a look at the top ISO 27001 consultants in the UK according to founders. For the first time ISO 27001 lead implementer, finding an ISO 27001 consultancy is often the quickest and easiest way to help you pass your ISO 27001 audit, however, with lots of consultants to choose from it’s important that you select the one best suited to your team and size.
| Number of Employees | Estimated Cost |
| 1-45 | £3,750 – £7,500 |
| 46-125 | £8,750 – £10,000 |
| 126 -425 | £11,250 – £12,500 |
| 426 – 625 | £13,750 |
| 626 – 875 | £15,000 |
| 876 – 1175 | £16,250 |
Frequently Asked Questions
ISO 27001 vs SOC2: How do they differ?
Both the ISO 27001 standard and SOC 2 state that organisations only need to adopt a control if it applies to them, but the way they approach this differs slightly.ISO 27001 focuses on the development and maintenance of an ISMS. In order to remain compliant, you must conduct a risk assessment, identify and implement security controls and regularly review their effectiveness.SOC 2, is much more flexible. It comprises five Trust Services Principles: Security, Availability, Processing Integrity, Confidentiality and Privacy, but only the first of those is mandatory.Overall, on the question of SOC2 vs ISO 27001, the former is easier and less expensive to implement and maintain, but it’s also less rigorous.
ISO 27001 vs Cyber Essentials: How do they differ?
The Cyber Essentials certification is required to be able to work with public bodies in the UK but is also very popular with private companies seeking to demonstrate data security.While ISO takes a risk-adjusted approach, where you as a company can apply a certain level of judgement about the amount of risk related to a control, CyberEssentials has a more rigid approach.For small companies this may result in a number of measure that have to be taken that in an ISO 270001 certification would have not been necessary due to a low amount of risk. For other companies however, for example larger enterprises, CyberEssentials may end up being less labour insensitive for the same reason. We can recommend CyberSmart to help you get CyberEssentials Plus certified.
What are the ISO 27001 security principals?
The three ISO 27001 security principals are confidentially, integrity and availability of data. Together, these three principles help organisations adopt an Information Security Management System (ISMS) that will help minimise the chances of an information security breach as well as limit its impact (if it still happens).
Should I buy an ISO 27001 toolkit?
If you’re a new ISO 27001 lead implementer then purchasing an ISO 27001 toolkit could be a good way to help with your ISO 27001 training whilst keeping your ISO 27001 cost down. An ISO 27001 toolkit will typically contain a list of templates such as an ISO 27001 risk assessment that allow you to speed up your ISO 27001 implementation process. Whilst ISO 27001 toolkits can speed up the time before you get an ISO 27001 auditor into to asses your business, they won’t be sufficient by themselves to get your through ISO 27001 certification and you should be careful to avoid businesses that overpromise in this area.
What are the ISO 27001 benefits?
The main ISO 27001 benefit is that it provides your business with greater quality assurance and higher levels of trust for stakeholders.The ISO 27001 auditing process follows a rigid framework, which results in a business adopting a set of ISO 27001 controls that demonstrate that data is being handled with integrity. Furthermore, ISO 27001 certification demonstrates that strategies are in place to continually review data handling processes & policies.
What are the ISO 27001 controls?
The ISO 27001 controls (Annex A controls) are split into 14 categories and within those there are 114 controls that are outlined as tools for effective risk management. Each category of ISO 27001 controls can be attributed to a different area of your business and they’re not all IT related. They range from organisational , IT, HR, legal and physical controls. ISO 27001 controls are implemented to mitigate risks identified in an ISO 27001 risk assessment, which your ISO 27001 auditor will ask to see evidence for during your audit.
How much does ISO 27001 certification cost?
ISO 27001 certification costs can be broken down into a few elements. The first is the cost of ISO 27001 training. An ISO 27001 lead implementer course can be around £2225 with a company such as BSI, however, if you're looking to keep the cost down, there is great free material from companies such as Advisera. The cost of an ISO 27001 toolkit would typically be into the low to mid hundreds of pounds.The second cost to take into account is that of an ISO 27001 consultant, which would typically be around £140 per hour. On average a business may need anywhere from 24 - 160 hours of ISO 27001 consultancy work in order to achieve ISO 27001 certification. This would put the cost between £3360 - £22,400.The ISO 27001 cost of auditing is typically based on the number of employees within an organisation. The range then depends on which ISO 27001 auditor you choose and how many on-site days and how many remote days they need to spend with your business to do their ISO 27001 auditing.



